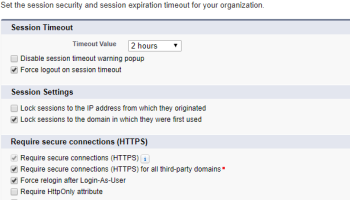
Require Secure Connections (https) For All Third-party Domains
Require secure connections (https) for all third-party domains. In the left menu click Settings Basic. In the top left click the Down arrow. Fixed - Summer 17 Patch 70.
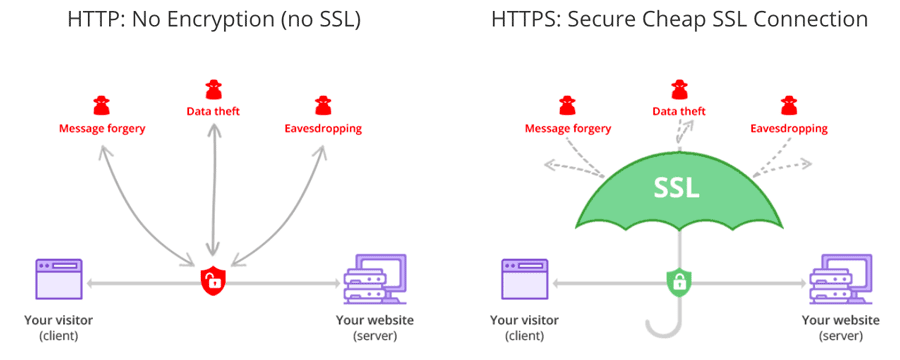
The permission is supposed to be OFF by default for existing organization and. As mentioned above Google began rolling out Chrome 68 in July 2018 marking a website as Not Secure if it is not protected with an SSL certificate. This includes all federal websites as well as federally operated HTTP-based APIs.
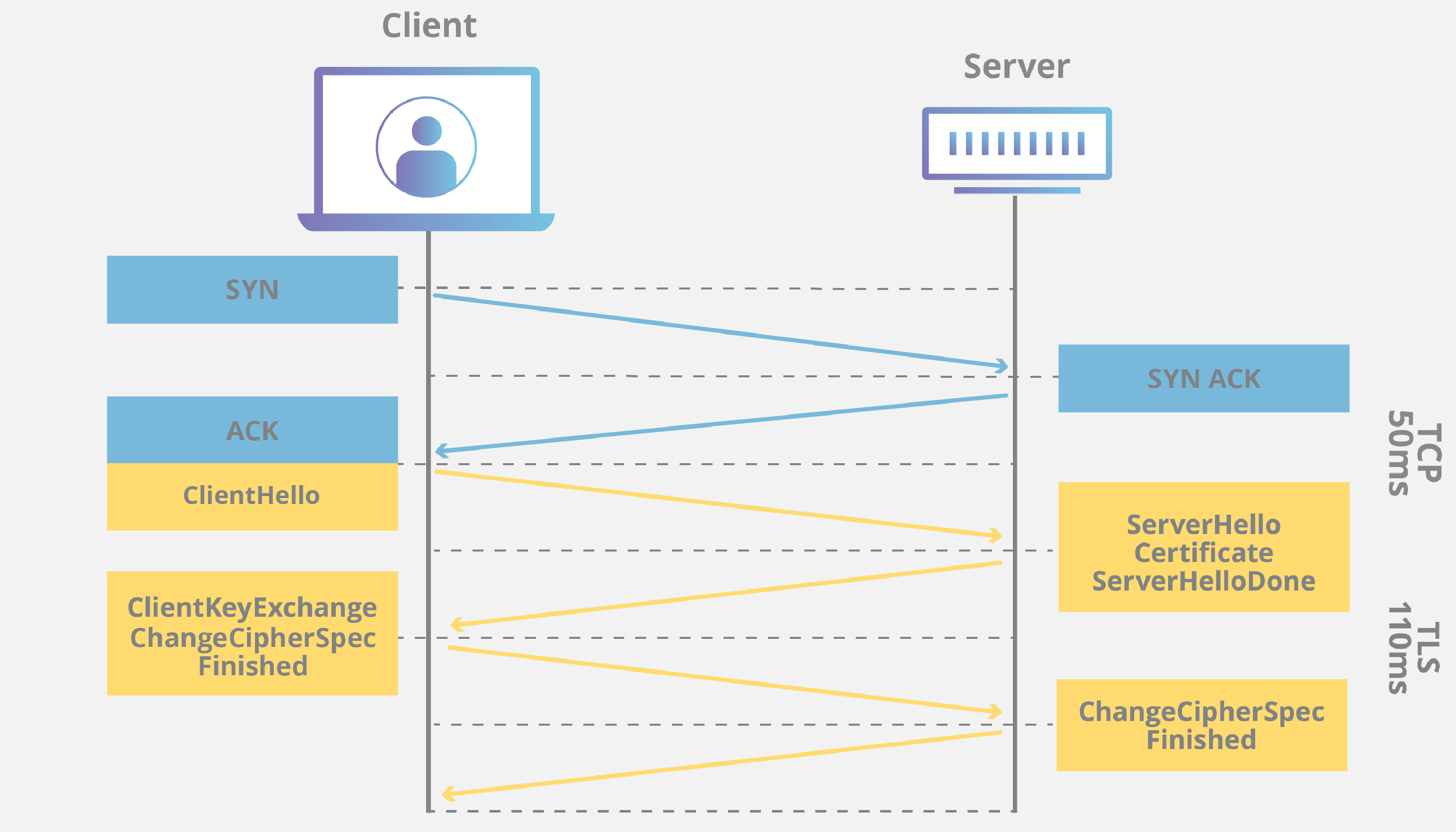
I have to increase the security level of my org. Select the Directory Security tab. In HTTP version 11 the secure connection is optional you may have HTTP andor HTTPS independent of each other while in HTTP2 it is practically mandatory even though the standard defines HTTP2 with or without TLS most browser vendors have stated that they will only implement support for HTTP2 over TLS.
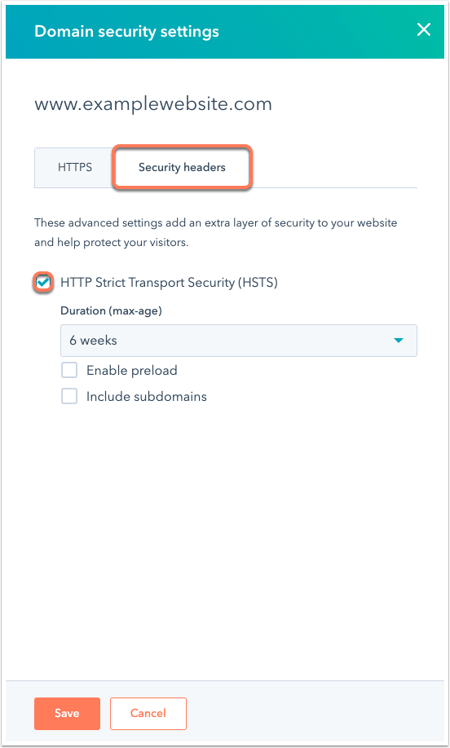
M-15-13 requires secure connections for websites and web services which means only HTTP-based protocols. Agencies must make all existing websites and services accessible through a secure connection HTTPS-only with HSTS by December 31 2016. However you can add TLS settings that require a secure connection for email to and from specific domains.
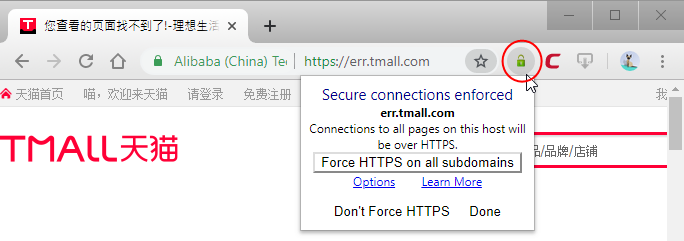
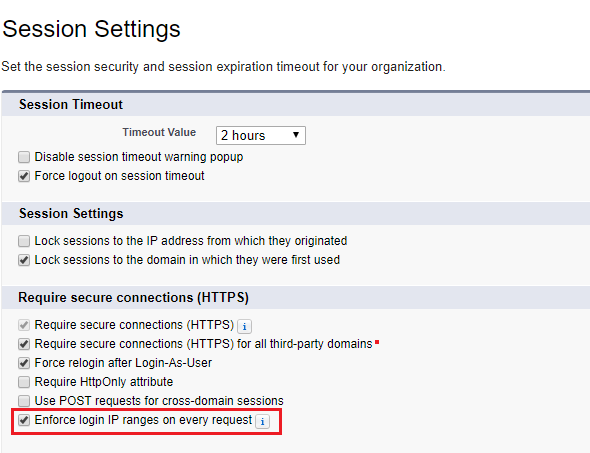
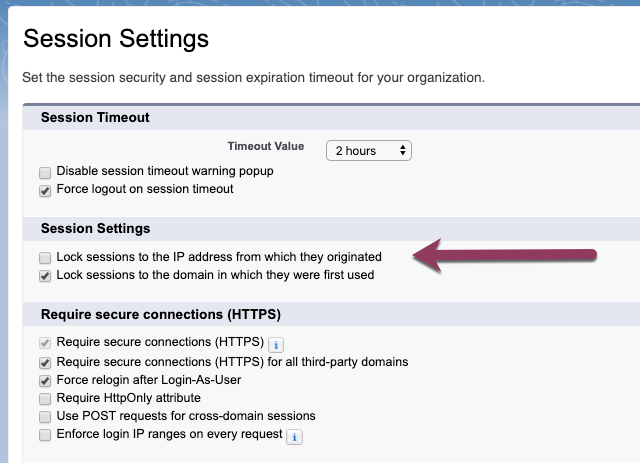
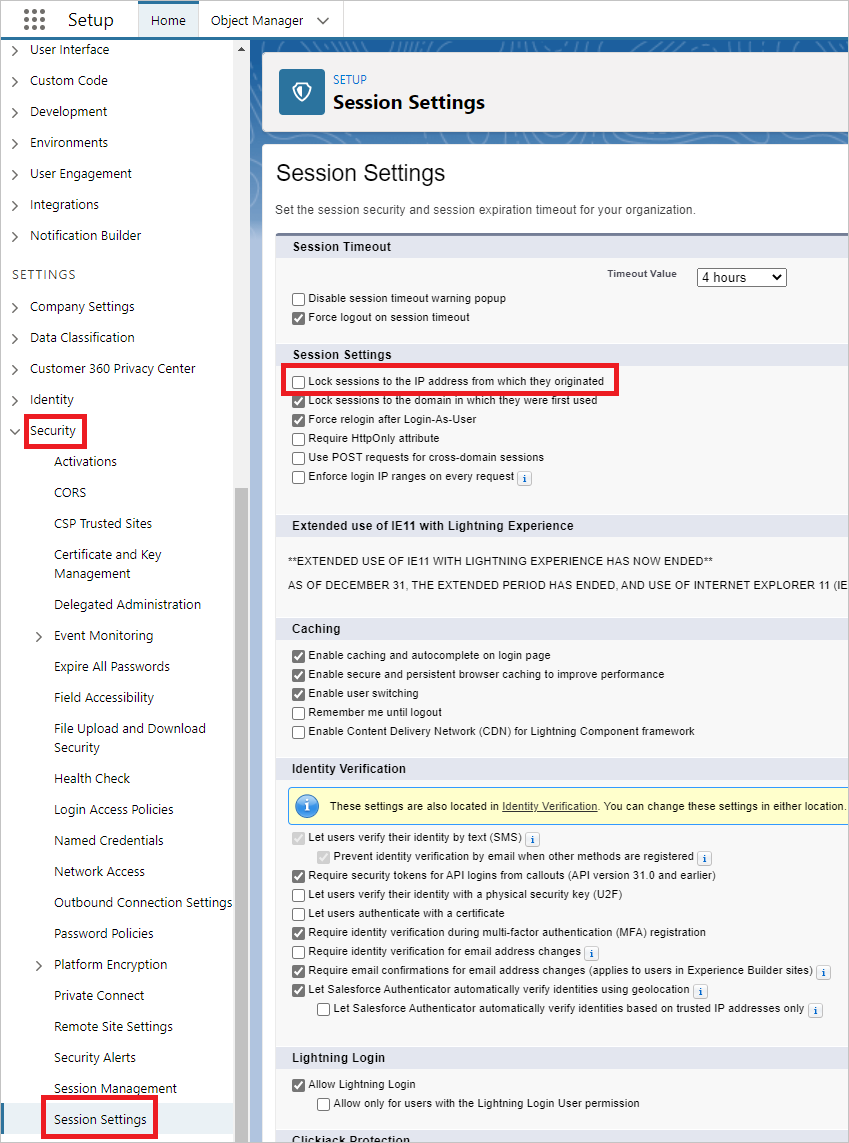
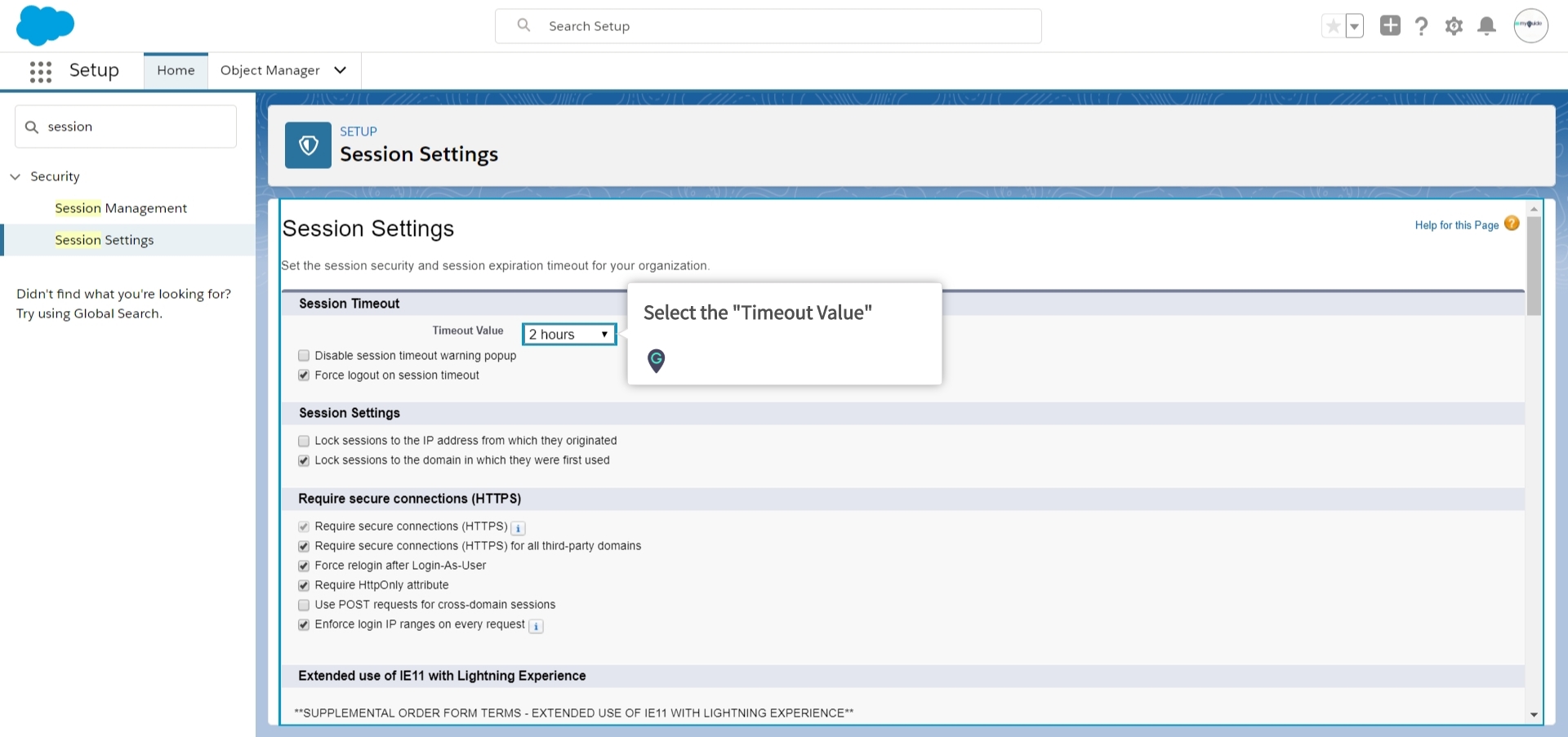
There is a new change to Session Settings including a new Permission titled Require secure connections HTTPS for all 3rd-party domains. HSTS tells the browser to request HTTPS pages automatically even if. On the right under HTTPS and HTTPS Availability select Yes.
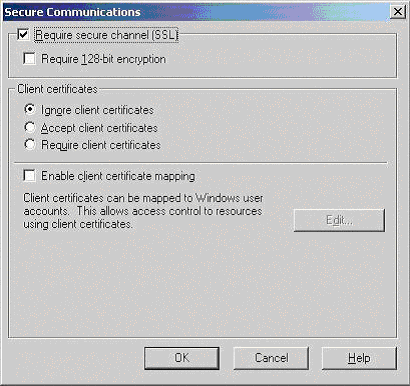
The use of HTTPS is encouraged on intranets but not explicitly required. Select Require Secure Channel SSL. Also add the certificate domain name that your partner organization uses to connect with Microsoft 365 or Office 365.
M-15-13 does not address the use of DNS or DNSSEC FTP or SFTP or any other non-HTTP network protocol. So if you have all secure servers youll always be connected securely.
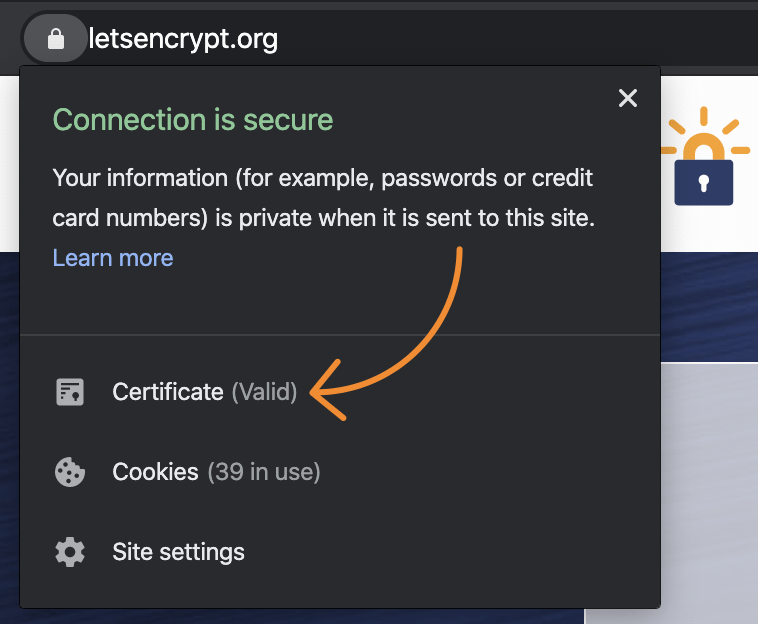
Its all a part of making the global web more secure.
This includes all federal websites as well as federally operated HTTP-based APIs. The server host name and cPanel username work together for a secure connection to happen. M-15-13 does not address the use of DNS or DNSSEC FTP or SFTP or any other non-HTTP network protocol. To fully mitigate the security issue for third-party devices you will need to complete all the steps. The Shared SSL looks identical to the Temporary URL except for the server name and username. Does your website really need an SSL certificate. Warning Starting February 2021 enforcement mode will be enabled on all Windows Domain Controllers and will block vulnerable connections from non-compliant devices. To do this use all the settings shown in Example 1. In the left menu click Settings Basic.
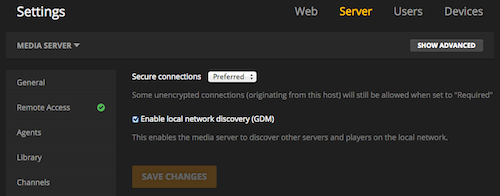
HSTS tells the browser to request HTTPS pages automatically even if. You can always manually go to httpsappplextvdesktop to force using a secure connection to Plex Web App. To monitor agency compliance a public dashboard has. HSTS tells the browser to request HTTPS pages automatically even if. On the right under HTTPS and HTTPS Availability select Yes. At that time you will not be able to disable enforcement mode. To do this use all the settings shown in Example 1.






















Post a Comment for "Require Secure Connections (https) For All Third-party Domains"